What happens when a single stolen cookie drains thousands in ad spend before you even notice?
A growing wave of Meta Business account hijacks has exposed how vulnerable marketing infrastructure can be when basic security hygiene lags behind evolving threats. The latest FileFix/StealC malware campaigns — which use fake Meta suspension pages to steal session data — are just one part of a broader shift: attackers are targeting ad dashboards, not databases.
Cybercriminals are chasing where the budgets live. Between malicious browser extensions and cloned Meta login portals, even experienced media buyers have become targets.
This guide breaks down how to close the gaps before they’re exploited: tightening access roles, enforcing SSO and 2FA, auditing extensions, and building an incident response plan that stops hijacks before they start.
The Rising Risk: Why Meta Ad Accounts Are Prime Targets
Meta ad accounts have evolved into lucrative, high-impact targets for cybercriminals. Beyond the immediate financial losses, a breach can expose brand assets, destroy campaign integrity, and damage client trust within hours.
In 2025, threat actors have intensified their focus on Meta Business accounts, blending phishing, social malware, and malicious extensions to gain persistent access.
Financial Payoff and Brand Exploitation
Ad accounts carry direct monetary value. Once inside, attackers can add payment methods, hijack live campaigns, and run fraudulent ads at scale. According to the Sift Digital Trust Index, 83% of digital businesses have faced at least one account-takeover attempt this year, with global losses from ATO fraud projected to surpass $17 billion in 2025, up from $13 billion the previous year.
These attacks are particularly damaging for marketers and agencies because compromised ad accounts can immediately be used to run unauthorized ads, change billing settings, and exploit stored payment credentials.
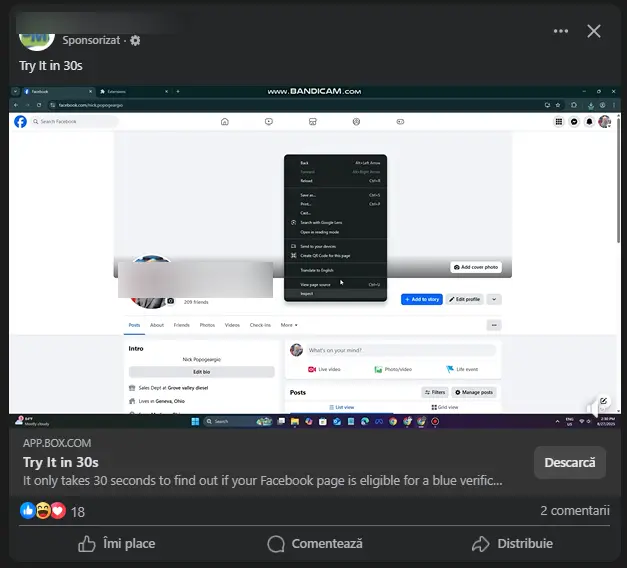
A clear example came to light in Bitdefender’s research on fake Chrome extensions impersonating Meta tools. These extensions harvested session cookies and hijacked ad accounts, redirecting spend toward crypto-scam campaigns and counterfeit product ads — all charged to the victim brand. Here's how one of these scams looks like:
The ad looks like a polished tutorial on how to install and use the software. But once hijacked, accounts would be recycled to promote more malicious links, creating a self-sustaining fraud loop.
Expanding Attack Surface Through Business Integrations
Meta Business Manager’s structure, where ad accounts, Pages, catalogs, and payment methods are interconnected, creates a single point of compromise. Once an attacker secures admin-level access, they can propagate through connected assets and escalate privileges.
A real-world case shared on Reddit’s /r/cybersecurity_help illustrates this risk: a verified business lost over $11,000 in ad spend within hours of a takeover, despite two-factor authentication being active. Attackers bypassed 2FA by stealing browser session cookies, enabling silent access that persisted until all tokens were revoked.
The Hacker News' report corroborates this trend, confirming that sophisticated malware operators now target business ad accounts through browser extensions and session hijacking rather than brute-force credential theft.
2025’s Emerging Threat: FileFix / StealC Campaigns
A new frontier in social-malware campaigns emerged with the FileFix/StealC incident, first detailed by Acronis Cyber Protect.
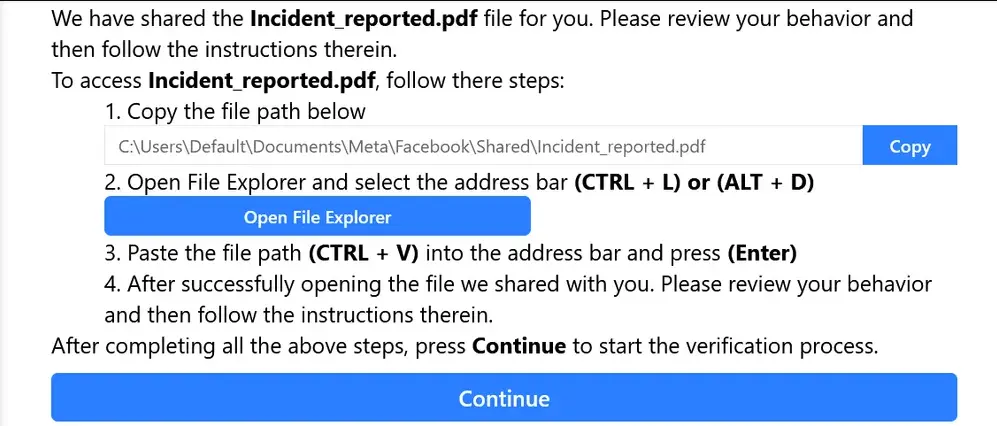
In this attack, threat actors sent fake Meta suspension notices to business users, leading them to cloned Meta Support pages. Once the victim ran the provided PowerShell “appeal script,” StealC malware was installed, exfiltrating browser cookies, credentials, and access tokens.
This effectively neutralized 2FA, granting full control over Meta Business assets and linked ad accounts.
Key Takeaway
In 2025, Meta ad accounts are not just marketing tools — they’re cyber-infrastructure assets. Criminal groups increasingly weaponize them for financial gain, ad fraud, and further malware distribution. Agencies and brands must now treat ad-account protection as a core cybersecurity function, not an IT afterthought.
Core Defense Layer: Role Hygiene and Access Control
Effective access control is foundational to securing your Meta Business Manager environment, especially for ad accounts. You must approach this from two interconnected angles: role hygiene (who has access and at what level) and access control audit routines (when and how you monitor and remove access).
Role Hygiene: Define Clearly, Enforce Minimally
Start by mapping who needs access to which asset — and give them only what they need. On Meta’s own help site, you’ll see that businesses can “manage the access and permissions people have to your business portfolio and business assets at any time.”
Here are best-practice principles for role hygiene:
- Least‐privilege rule: Only assign Admin roles to those who must add/remove users, change billing, or overhaul asset structure. For standard campaign creators or analysts, use roles like Advertiser or Analyst. For example, a third-party agency granted “Advertiser” access can run campaigns but cannot change payment methods or remove other users.
- Segment roles by function: Separate roles for creative/placement, billing/payment, and data access. If someone leaves the team, you revoke only the finance access rather than full asset control.
- Agency/Partner access via Business ID: If you work with external agencies, invite them as a Partner with specific ad-account or Page roles rather than giving your agency user Admin rights on your business account.
- No shared logins: Each user should have their own login. Meta’s best practices flag people having access without two-factor authentication as a risk and specifically recommend removing users “without two‐factor authentication” or “with public email domains.”
Access Control Audit Routines: Review & Revoke
Assigning roles is only half the work. Regular audits service the hygiene part to ensure access remains tight.
Key checklist items:
- Monthly user-role review: Identify all active users in your business account and verify if their roles still match their responsibilities.
- Remove stale access: Users who’ve left the agency or switched roles should have their access removed promptly. Meta recommends removing inactive users.
- Review partner/agency access: Check partner roles and confirm they still require the permissions you’ve granted. If the scope of the engagement changed, reduce their role accordingly.
- Audit third-party integrations and token scopes: Check which apps or systems are connected to your ad accounts. Each API or automation tool should have minimal permissions and be subject to review.
- Incident‐ready logs of access changes: Every time a role is added/removed, or an ad account is handed over, record the change with timestamp, user responsible, and reason. This creates a trail for incident response and audit.
In summary, securing your Meta ad-account environment starts with role hygiene (who gets what access) and is sustained by regular audits (when you review and revoke). Think of it as access control being your primary lock — and the audit routines as your regular lock-maintenance.
Authentication and Token Security
Even with clean role assignments, compromised authentication flows and API tokens remain one of the biggest vectors for Meta ad-account hijacks. Attackers rarely brute-force passwords anymore; instead, they steal session cookies, bypass 2FA through infostealers, or abuse third-party integrations that retain elevated permissions.
Strengthening Authentication: From 2FA to SSO Enforcement
The first line of defense is ensuring all users in Meta Business Manager have two-factor authentication (2FA) enabled. Meta officially states that “people with access to your business without two-factor authentication are a security risk,” and recommends enforcing it across all users.
However, 2FA alone isn’t enough when browser sessions are stolen, as seen in the FileFix/StealC campaign. This 2025 attack distributed fake “Meta suspension” notices that lured users into executing PowerShell scripts to install the StealC infostealer, which extracted authentication cookies from Chrome, bypassing both passwords and 2FA.
To mitigate this, agencies and larger brands should integrate Single Sign-On (SSO) through identity providers such as Okta, Microsoft Entra ID, or Google Workspace. SSO enforces corporate credential standards (strong passwords, session timeouts, and device checks) while allowing centralized revocation if an employee leaves.
Here's a simple explanation of what SSO is by TikTok creator Tiff in Tech:
@tiffintech Here is a simple way to understand what SSO is whether you are technical or not 💡 #stem #techexplained #learnontiktok #techtips
Meta supports SSO via its Enterprise Identity Management option for Business Accounts, giving security teams visibility over login endpoints.
Token and Integration Security
Beyond human logins, many marketers rely on automation tools (for reporting, scheduling, or campaign optimization) that use Meta API access tokens. These tokens can persist for weeks or months and often have broad scopes, making them attractive to attackers.
To reduce risk:
- Audit connected apps monthly: Navigate to Business Settings → Integrations → Business Apps and remove any tool no longer in use.
- Restrict token scopes: Ensure tokens are limited to the minimum API endpoints needed (e.g., ads_read, not ads_management, unless essential).
- Rotate API tokens quarterly: Expire tokens manually or via your integration’s admin console to limit persistence if one is compromised.
- Centralize API oversight: Keep a single spreadsheet or logging system that tracks each token’s creation date, owner, and associated permissions.
Key Takeaways
Treat every access credential — human or machine — as a potential breach vector. Passwords are no longer the point of failure; session cookies and API tokens are. Strengthening authentication and tightening integration scopes now form the backbone of Meta ad-account security in 2025.
Detecting and Blocking Malvertising Threats
While stolen tokens and weak access controls create the entry point, malvertising is how many Meta ad-account hijacks begin. These campaigns exploit marketers’ daily workflows — fake Meta alerts, fraudulent browser extensions, and cloned login portals — to plant credential-stealing malware directly on the systems managing ad spend.
In 2025, these threats have evolved beyond email phishing into multi-channel deception networks targeting business accounts.
Recognizing Fake Meta Notices and Cloned Portals
Cybercriminals increasingly impersonate Meta’s enforcement teams to trick marketers into “appealing” account suspensions. Victims receive emails claiming ad policy violations, leading to fake “Meta Business Support” pages that perfectly replicate Meta’s domain styling.
These portals deliver scripts disguised as account-verification tools — but in reality, they install malware like StealC or Rhadamanthys, which extract cookies, session tokens, and saved logins.
Security firm Acronis, as mentioned before, confirmed that the FileFix variant embedded payloads inside seemingly harmless images (steganography), enabling silent credential theft even when downloads were scanned by endpoint protection.
The goal isn’t immediate damage — it’s persistence: keeping long-term access to ad accounts to run malicious campaigns weeks later.
Auditing and Controlling Browser Extensions
Marketers are uniquely exposed because browser extensions often request wide access permissions to Business Manager, Ads Manager, or analytics dashboards. In Bitdefender’s 2025 HotforSecurity report, researchers documented a campaign that distributed fake “Meta Verified” and “Pixel Helper” add-ons via sponsored Facebook ads.
Once installed, these extensions captured access tokens and relayed them to Telegram-controlled servers, granting attackers real-time control of business accounts.
To mitigate this threat:
- Conduct a quarterly extension audit on every system that accesses Meta Business Manager. Remove any add-ons that are inactive, unofficial, or lack reviews on the Chrome Web Store.
- Use enterprise device policies (via Google Admin or Microsoft Intune) to whitelist approved extensions only.
- Monitor your Meta Security Center for unfamiliar app authorizations under Business Settings → Integrations → Apps and Services.
Monitoring for Campaign-Level Red Flags
Even if malware is undetected at the device level, malvertising behavior leaves traces inside Meta’s own environment. The SC Media brief on Meta malvertising campaigns
highlights recurring anomalies security teams should flag:
- Campaigns launched outside normal business hours.
- Sudden budget spikes tied to new payment methods.
- Ads approved that redirect to external domains or crypto wallets.
- Duplicate campaigns are running under non-admin users.
Meta recommends using Ad Account Activity Logs and Ad Delivery Insights to detect unauthorized changes quickly. Suspicious creative approvals or unrecognized billing profiles should trigger immediate role lockdown and API token rotation.
Key Takeaway
Malvertising isn’t just a nuisance — it’s the delivery system for credential theft and persistent hijack operations. Routine extension audits, user-awareness training, and anomaly monitoring inside Meta’s own dashboards now form the most practical defense against these stealth campaigns.
Lock the Doors Before the Clicks
Meta ad-account hijacks aren’t just IT problems — they’re marketing crises waiting to happen. In 2025, social-malware campaigns, fake Meta alerts, and malicious extensions have made advertising dashboards one of the most targeted assets in digital business.
The solution isn’t one magic control, but a security culture: strict role hygiene, enforced 2FA and SSO, regular token reviews, and extension audits that keep every login clean.
For brands and agencies managing multiple accounts, prevention is far cheaper than recovery. One stolen token or overlooked admin role can cascade into lost spend, client data exposure, and reputational damage. Treat your Meta Business Manager like a financial system — not a social app — and make access reviews as routine as campaign approvals.
By institutionalizing these safeguards now, teams can stop hijacks before they start and protect the trust that drives every paid impression.
Frequently Asked Questions
How can marketers ensure authentication is strong enough for shared ad accounts?
Teams should go beyond passwords and implement multi-layer identity checks across platforms. Using higher levels of authentication such as device-based approval and biometrics minimizes the risk of credential theft, especially when multiple users access Meta Business Manager.
What lessons from affiliate programs can improve ad-account fraud prevention?
Affiliate marketers rely on rigorous verification to block click fraud and payout abuse. Ad managers can borrow similar fraud prevention practices—like anomaly detection, IP monitoring, and transaction logs—to identify unauthorized campaign activity early.
How do other platforms handle sensitive user data differently from Meta?
When TikTok strengthened its U.S. data security with localized storage and transparency programs, it set a precedent for how social networks can safeguard operational access. Meta teams should mirror that approach by isolating ad data and limiting third-party integrations.
Why should marketers regularly test domain certificates and ad landing pages?
Compromised SSL certificates can expose both campaign links and Business Manager logins to phishing intermediaries. Running periodic checks with SSL auditing tools ensures encryption remains valid and eliminates one of the easiest exploits for attackers.
Could encrypted messaging tools improve internal ad-team communication security?
Yes — secure channels with end-to-end encryption and expiring messages reduce social-engineering risks during campaign coordination. Platforms offering vanishing messages and Bitcoin-style encryption help ensure that sensitive links, credentials, and approvals never persist in unsecured chats.